Writing Code That Lasts: A Battle-Tested Approach to Development
I’ve written code I’m proud of and code that haunted me in production at 3 AM. The difference? It’s rarely about clever algorithms or cutting-edge frameworks. It’s about discipline, pragmatism, and respect for the people who’ll maintain your work—including future you.
Here’s what I’ve learned about building software that actually ships, scales, and survives contact with reality.
Requirements: Your North Star in the Chaos
It’s tempting to dive straight into coding, especially when you’re excited about a solution. Resist that urge.
I keep the requirements document open while coding and review it at the start of each feature. Not because I doubt my memory, but because requirements are my contract with stakeholders. Every function, every class, every decision should trace back to a requirement—functional or non-functional.
When I’m tempted to add something “cool” that wasn’t requested, I ask myself: “Does this solve a stated problem, or am I just showing off?” Usually it’s the latter. Save those ideas for the backlog. Ship what was promised first.
Reality check: Requirements evolve. When they do (and they will), update documentation immediately and communicate changes to the team. Drift between code and requirements is how bugs hide.
Architecture: Follow the Blueprint, But Know When to Adapt
A good architecture gives you guidelines, not handcuffs. I implement the designed architecture faithfully, but I’m not dogmatic about it.
If the architecture calls for a microservice but your feature is genuinely simple, don’t over-engineer it. Conversely, if you discover during implementation that a module needs better separation than originally planned, speak up early. Architecture decisions made without implementation context are educated guesses—sometimes they need refinement.
Focus on bounded contexts and clear interfaces. When modules communicate through well-defined contracts, you can change implementations without cascading failures. That’s the real win.
Clean Code: Write for Humans First, Machines Second
Computers execute code, but humans maintain it. I’ve spent more time reading code than writing it, and I bet you have too.
Here’s my hierarchy of code quality:
1. Clarity over cleverness. That one-liner you’re proud of? If it requires a comment to explain, break it into readable steps.
2. Names matter more than you think. ‘getUserData()’ tells me nothing. ‘fetchActiveUserProfileWithPreferences()’ tells me everything. Be specific.
3. Functions should do one thing. If you can’t describe a function in a simple sentence without using “and,” it’s doing too much.
4. Consistency trumps personal preference. Follow the team’s style guide religiously. Automated formatters (Prettier, Black, gofmt) eliminate debates. Use them.
I aim for code that reads like prose. When another developer can understand the flow without jumping between files constantly, you’ve succeeded.
Performance: Optimize the Right Things at the Right Time
“Premature optimization is the root of all evil,” Knuth said, and he was right. But shipping slow code is also evil.
Here’s my approach: write clear code first, then measure. Profile before optimizing. I’ve been surprised too many times by what’s actually slow versus what I assumed was slow.
Focus optimization efforts on:
- Hot paths: Code that runs frequently or in critical user flows
- Database queries: Usually the first bottleneck (N+1 queries, missing indexes)
- Network calls: Reduce round trips, batch requests, cache aggressively
- Memory allocation: In high-throughput systems, allocations can kill performance
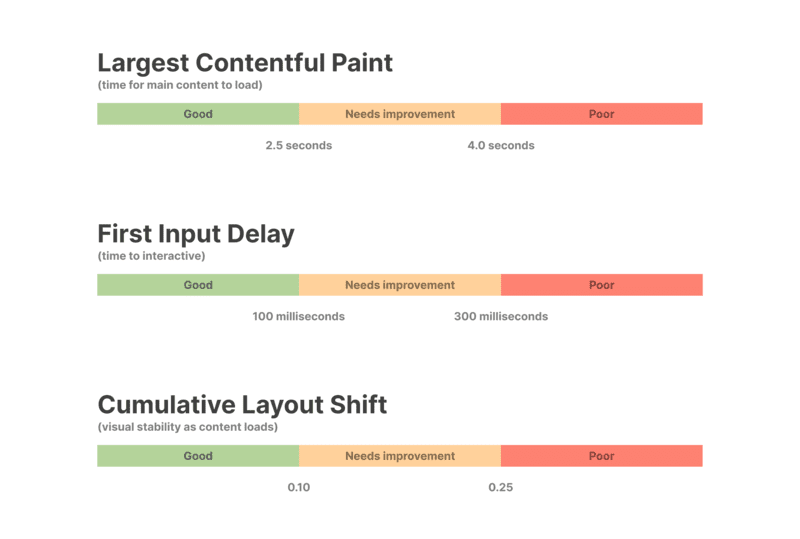
Set performance budgets early (page load under 2 seconds, API response under 200ms) and track them in CI. What gets measured gets managed.
Security: Bake It In, Don’t Bolt It On
Every line of code is a potential vulnerability. I’ve learned to think adversarially while coding—if I were trying to break this, how would I do it?
My non-negotiable security practices:
- Validate all input. Never trust user data. Sanitize, validate types, check ranges. Every. Single. Time.
- Use parameterized queries. SQL injection still tops vulnerability lists because developers still concatenate strings.
- Hash, don’t encrypt passwords. Use bcrypt, scrypt, or Argon2. If you’re rolling your own crypto, you’re wrong.
- Implement least privilege. Users and services should have minimum necessary permissions.
- Keep dependencies updated. Automate security scanning with tools like Dependabot or Snyk.
When in doubt, follow OWASP guidelines for your stack. Don’t reinvent security mechanisms—use battle-tested libraries.
Error Handling: Fail Gracefully, Debug Efficiently
Exceptions will happen. Hardware fails, networks timeout, users input unexpected data. Your job is handling failure elegantly.
I structure error handling in layers:
- Validate early to catch bad input before it propagates
- Fail fast when continuing would corrupt state
- Provide context in error messages—log what went wrong and why
- Distinguish recoverable from fatal errors and handle appropriately
Log strategically, not exhaustively. I include: timestamp, severity, context (user ID, request ID), error details, and stack traces for exceptions. Structure logs as JSON for easy parsing. Avoid logging sensitive data like passwords, tokens, or PII.
Critical insight: Error messages for users should be helpful but vague about internals. Detailed errors go in logs, not response bodies.
CI/CD: Automate the Boring, Error-Prone Stuff
Manual deployments are where mistakes happen. I automate everything that can be automated.
My standard CI/CD pipeline:
- Linting and formatting checks (fail fast on style violations)
- Unit tests (quick feedback loop)
- Integration tests (verify components work together)
- Security scanning (catch known vulnerabilities)
- Build artifacts (containers, packages)
- Deploy to staging (automated for main branch)
- Deploy to production (automated or one-click after verification)
Feature flags let me deploy code without enabling features. This decouples deployment from release, reducing risk and enabling gradual rollouts.
Time saver: Good CI/CD pipelines catch issues in minutes, not hours or days. Invest in making them fast.
Documentation: Write Docs That You’d Want to Read
Documentation isn’t optional overhead—it’s how your code survives your absence.
I document at multiple levels:
Code comments explain why, not what. The code already shows what it does. Comments explain business logic, gotchas, or non-obvious decisions.
Function documentation describes purpose, parameters, return values, and side effects. I use docstrings that tooling can parse (JSDoc, Python docstrings, Javadoc).
Module READMEs provide architectural overview, setup instructions, and common use cases.
API documentation is auto-generated from code (OpenAPI/Swagger). Keep it current by making it part of the build process.
Write documentation as you code, not after. Future you will be grateful when you return to code six months later with zero memory of why you made that weird architectural decision.
Testing: Your Safety Net for Change
I used to think tests slowed me down. Then I spent three days debugging a “simple” change that broke five things I didn’t expect. Now I test everything.
Unit tests verify individual functions in isolation. I aim for 80%+ coverage on business logic. Test edge cases, error conditions, and boundary values—not just the happy path.
Integration tests ensure modules interact correctly. Mock external services but test real integrations in staging.
End-to-end tests validate critical user flows. Keep these minimal (they’re slow and brittle) but cover your money-making paths.
I practice test-driven development for complex logic. Writing tests first clarifies requirements and produces better-designed code. But I’m pragmatic—simple CRUD operations don’t always need TDD.
Pro tip: Flaky tests are worse than no tests. Fix or delete them immediately. Teams lose trust in test suites when they can’t rely on results.
Dependencies: Manage Carefully, Update Regularly
Every dependency is code you’re responsible for but didn’t write. Choose wisely.
Before adding a library, I ask:
- Is it actively maintained?
- Does it have a reasonable security track record?
- Can I accomplish this with existing dependencies?
- What’s the bundle size impact (for frontend)?
Pin major versions but allow patch updates. Use lock files (package-lock.json, Gemfile.lock) to ensure reproducible builds. Review dependency updates for breaking changes before merging.
Monitor for vulnerabilities and update regularly. Letting dependencies rot for months makes updates painful. Small, frequent updates are safer than massive quarterly upgrades.
Scalability: Design for Growth, Build for Today
Scalability is about making smart trade-offs, not over-engineering everything.
I design for horizontal scalability by default—adding more servers should improve capacity. This means:
- Stateless services where possible
- Externalized session storage (Redis, database)
- Database read replicas for read-heavy workloads
- Asynchronous processing for heavy operations (queues, workers)
But I don’t build distributed systems when a monolith will do. Start simple and extract services when performance demands it or team structure requires it. Premature distribution creates complexity without benefit.
Use cloud-native services (managed databases, load balancers, auto-scaling groups) to handle scaling concerns. Let experts manage infrastructure so you can focus on application logic.
Maintainability: The Gift That Keeps Giving
Maintainable code is modular, tested, documented, and consistent. It’s code you can modify confidently without breaking the world.
I achieve maintainability through:
- Separation of concerns: Business logic, data access, presentation all separated
- SOLID principles: Especially single responsibility and dependency inversion
- Low coupling, high cohesion: Modules should be independent but internally focused
- Refactoring regularly: Don’t let technical debt accumulate
Leave code better than you found it. Fix small issues as you encounter them. Refactor mercilessly when safe to do so. Technical debt is like financial debt—a little is fine, but too much will bankrupt you.
Version Control: Your Time Machine
Git isn’t just backup—it’s documentation of how the system evolved.
I write commit messages that explain why changes were made, not just what changed. Future developers (including me) need to understand intent, not just implementation.
Use feature branches for new work. Keep main/master stable and deployable at all times. Practice trunk-based development for faster feedback—merge to main frequently (daily if possible) behind feature flags.
Review your own PRs before requesting review from others. Catch obvious mistakes and clean up commits. Respect your reviewers’ time.
Monitoring: Know What’s Happening in Production
Code isn’t done when it’s deployed—that’s when the real test begins.
I instrument code with metrics and logging from day one:
- Application metrics: Request rates, error rates, latency percentiles
- Business metrics: Conversions, signups, key user actions
- Infrastructure metrics: CPU, memory, disk, network
Set up alerts for anomalies. I prefer alerting on symptoms (high error rates, slow responses) over causes (high CPU). Symptoms affect users; causes might not.
Use distributed tracing for microservices. When requests span multiple services, tracing shows you the complete picture.
Learn from production: When issues occur, treat them as learning opportunities. Conduct blameless postmortems and improve systems based on what you discover.
Bringing It All Together
Great code isn’t about perfection—it’s about balancing trade-offs intelligently. Write code that’s clear enough to understand, tested enough to trust, documented enough to maintain, and performant enough to satisfy users.
Focus on fundamentals: clear requirements, solid architecture, clean code, comprehensive tests, and robust monitoring. Get these right and the rest falls into place.
Remember: you’re not just writing code for machines to execute. You’re writing for teammates to understand, for stakeholders to trust, and for users to rely on. Code with empathy, ship with confidence, and always be learning from what happens next.
The best developers I know aren’t the ones who write the cleverest code—they’re the ones whose code is still running smoothly years later, maintained by developers who appreciate the care that went into it.